Cybersecurity Metrics: Measuring Effectiveness of Your Security Measures
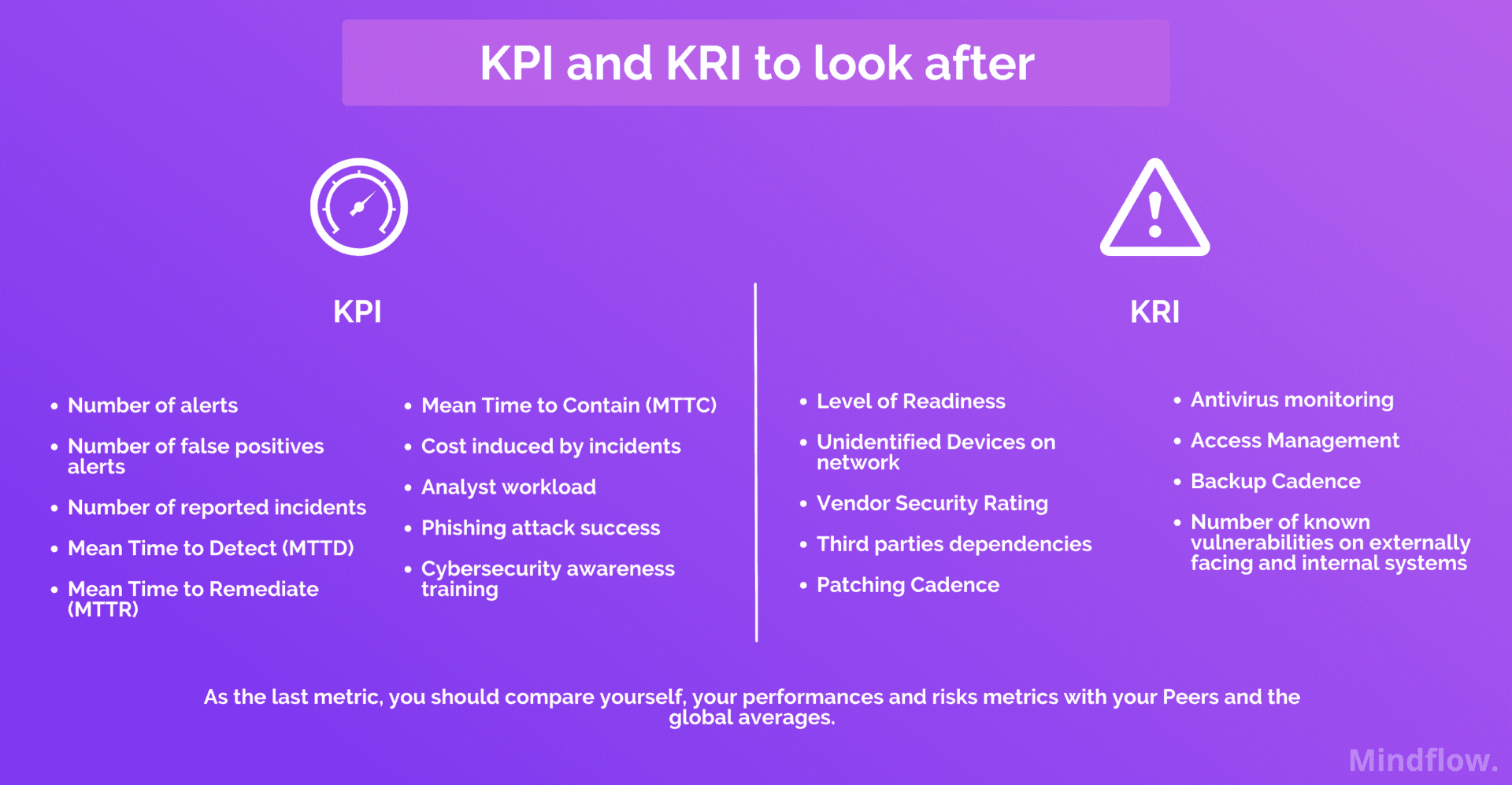
Cybersecurity Metrics: Measuring the Effectiveness of Your Security Measures In today’s increasingly digital landscape, where cyber threats are both pervasive ...
Read more
The Future of Cybersecurity: Trends Shaping the Digital Landscape
The Future of Cybersecurity: Trends Shaping the Digital Landscape As we advance further into the digital age, cybersecurity remains a ...
Read more
Understanding Malware Types: Protecting Your System from Harmful Software
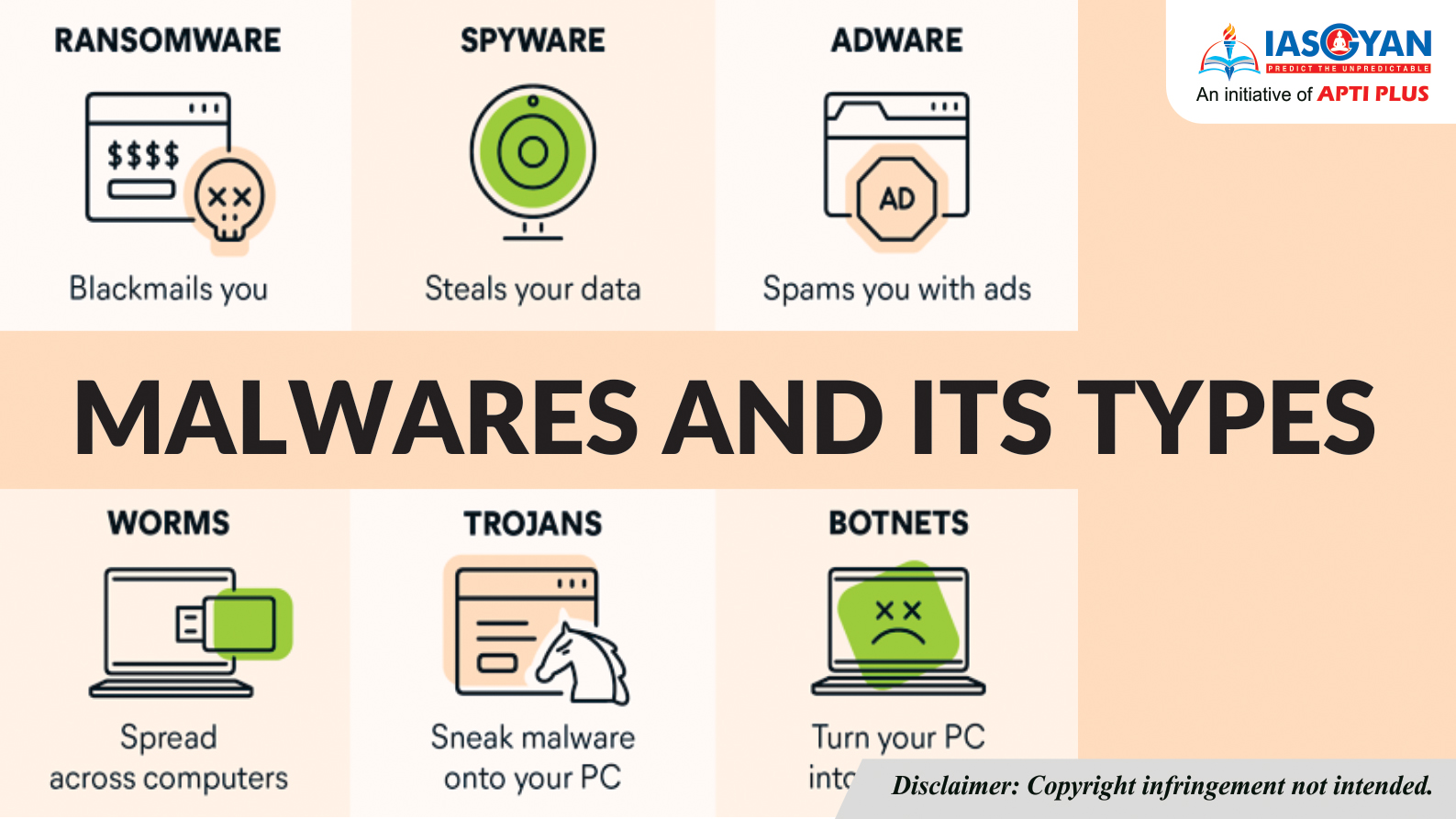
Understanding Malware Types: Protecting Your System from Harmful Software In the digital age, where technology is deeply integrated into our ...
Read more
Social Engineering Tactics: Recognizing and Defending Against Cyber Threats
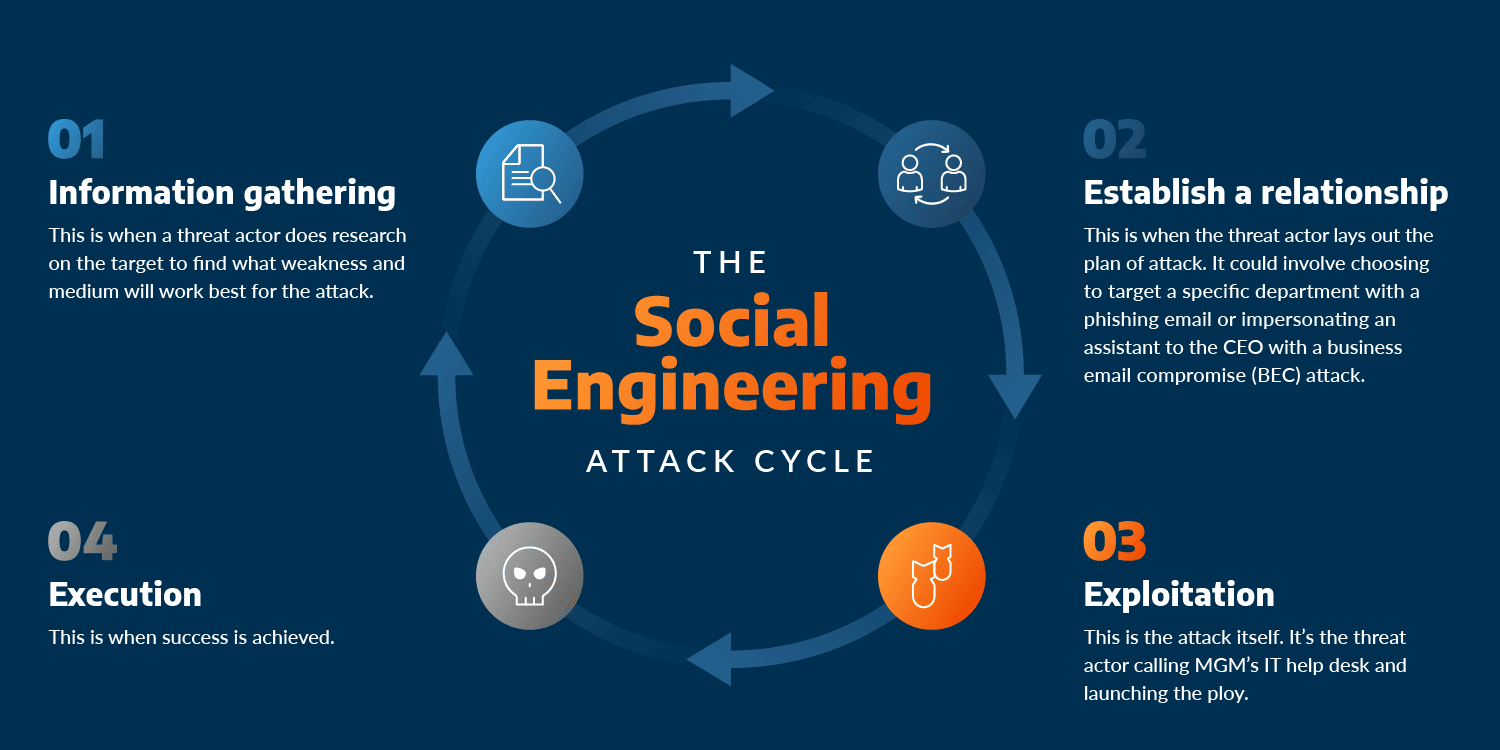
Social Engineering Tactics: Recognizing and Defending Against Cyber Threats In an age where technology is integrated into nearly every aspect ...
Read more
Mobile Security Threats: Protecting Your Devices from Cyber Attacks

Mobile Security Threats: Protecting Your Devices from Cyber Attacks As mobile devices become ubiquitous in our daily lives, they also ...
Read more
The Role of Encryption in Enhancing Cybersecurity for Businesses

The Role of Encryption in Enhancing Cybersecurity for Businesses In today’s digital landscape, where data breaches and cyber threats are ...
Read more
Cybersecurity Compliance: Meeting Regulatory Standards to Protect Your Organization

Cybersecurity Compliance: Meeting Regulatory Standards to Protect Your Organization In an increasingly digital world, the importance of cybersecurity cannot be ...
Read more
IoT Security Challenges: Protecting Devices in a Connected World

IoT Security Challenges: Protecting Devices in a Connected World The Internet of Things (IoT) has transformed the way we live ...
Read more
Cloud Security Best Practices: Safeguarding Data in the Cloud
Cloud Security Best Practices: Safeguarding Data in the Cloud As organizations increasingly adopt cloud computing to enhance efficiency, scalability, and ...
Read more
Incident Response Plans: Preparing for Cybersecurity Breaches and Attacks

Incident Response Plans: Preparing for Cybersecurity Breaches and Attacks In an era where cyber threats are increasingly sophisticated and prevalent, ...
Read more